Your home network’s security is only as good as the configuration of your router or gateway. Leave it open or vulnerable, and you might end up with freeloaders that hog your bandwidth, at best. At worst, a snoop might take the opportunity to examine your internal traffic, hoping to learn sensitive information about you that can be exploited.
To ensure that only approved devices are connected to your network, you can take a few simple steps to strengthen its security, which we explain below. If you can’t access some of these settings in your gateway (the combination modem/router provided by your internet service provider), consider switching off the router part of it and using a dedicated router instead, either of the traditional or mesh variety.
Change your passwords
Depending on your router’s age, you may need to change both the administrator password (which gives access to the management interface) and also the Wi-Fi password.
Older routers usually default to ultra simple passwords for the administrator account —think “admin” and “password”—and they’re easily found on online. You may have also chosen a simple, crackable password when turning on encryption for your network. For both scenarios, choose a new, stronger replacement. The best way to do this is a built-in password generator in a password manager—they’ll be truly random and thus more secure, and the manager will ensure you don’t forget it. (Good free password managers exist, so solid online security doesn’t have to cost you a thing.)
For newer routers, they often come with random passwords as default. It doesn’t hurt to change those if your router or gateway has that info printed on them though, particularly if you have less control over who might have physical access to the device. Just be sure to keep track of your new passwords, ideally in a password manager as mentioned.
Enable encryption
 Metamorworks / Getty Images
Metamorworks / Getty ImagesYou should always encrypt your network traffic. These days, choose WPA2 for the best security. Older protocols like WPA and the ancient WEP won’t adequately protect you. If your router supports the newer WPA3 protocol, you can try it out—it’s an improvement over WPA2—but all of your connecting devices must support that protocol. Most people can stick with WPA2 for now, and then flip over to WP3 once all devices in the household can also make the leap.
When setting up WPA2 encryption, pick WPA2 Personal if given a choice between that and WPA2 Enterprise in your router settings. Also, if you see TKIP and AES as different encryption options, go with AES as it’s much stronger.
For older devices that cap out at WPA, consider upgrading your router at last. You’ll get better security, faster speeds, and more features for as little as $50 (or less if you wait for a sale). If you’re on an ancient router that only has WEP, replace it stat. You’re barely one step above having an open network.
As for folks who leave encryption off because you want to share your internet with others: We salute your altruism, but don’t let that come back to haunt you. As mentioned above, no encryption means that people can spy on your internet traffic, giving them clues to your activities (including banking). That could lead to troublesome problems down the road.
Change your SSID
 CloudTrax
CloudTrax
Name your network wisely. It should be something generic but not too common that doesn’t reveal your address.
A Service Set Identifier (SSID) is the name of a wireless network. That is what you see when trying to connect to a Wi-Fi network: Linksys616, D-Link2289, 555MainSt, We Have No Wi-Fi Here, etc.
Because older routers default to ultra-simple or easily cracked passwords, changing the SSID to a non-identifying word or phrase helps thwart hackers looking for low-hanging fruit. Leave it as linksys, and a savvy snoop may realize you’re running a much older Linksys router with “admin” as the password for router management. If you haven’t changed that password (and most people don’t), your home network is ripe for their exploration.
As you move forward in time, many routers use a combination of the manufacturer name and numeric string (often the model number) for the SSID—making it even easier to look up the default admin password. Unless you have a modern enough router that issues random passwords as part of the factory settings, you could be even more vulnerable. So just change the SSID. (Don’t use your address for it, either. No need to make yourself more identifiable.)
Note: Years ago, a common recommendation used to be to not broadcast your SSID: that is, keep it hidden from the list of available Wi-Fi networks in your vicinity. But trying to do security through obfuscation doesn’t really work here—it’s been proven that someone can easily discover hidden networks with a wireless spectrum scanner. Since disabling SSID broadcasting also makes it harder for people to join your network, you’re generally better off leaving it visible, using the strongest encryption available to you, and creating a very strong Wi-Fi password.
Turn off remote access
Some routers allow you to access the administrator account from outside your home network. Disable this feature. Extremely few people need to leave this on, and by turning it off, someone will have to be in range of your router and successfully connect to it to attempt mischief. You can then protect yourself against the latter scenario by enabling encryption, changing your SSID, and turning off WPS (detailed below).
Disable Wi-Fi Protected Setup (WPS)
 TP-Link
TP-Link
On this older TP-Link router (circa 2010), you can activate WPS by pressing a button.
WPA2 and the older WPA protocol require more complicated passwords for Wi-Fi access. So to simplify connecting to those types of networks, router manufacturers began offering Wi-Fi Protected Setup, or WPS, as a feature. But it can be easily cracked, and so you should disable it despite its time-saving intentions.
Think of this feature as akin to setting both a password and another, less complex form of authentication on the same device. On a Windows 10 PC or a modern mobile device, that might be a personal identification number (PIN) or registering a fingerprint. Instead of entering your password, you can simply enter the shorter PIN or hold your finger against a reader.
WPS works similarly, except it’s baked in as a default part of your settings. The two common methods for implementation are either an eight-digit PIN or a button you push on the router (either physically or virtually) to authenticate a device and allow it onto your network. The PIN method is the more vulnerable of the two: Hackers can guess the PIN through brute force—and possibly lock up your router as the cracking happens, which effectively causes a denial-of-service attack on your network.
As for the push-button method, anyone with physical access to your router can still use it as a roundabout way to determine your Wi-Fi password—so if you’re trying to keep access restricted, you can undermine your efforts by leaving this feature active.
Keep your router’s firmware updated
Over time, vulnerabilities can be discovered in your router’s existing firmware. Performing regular updates will help patch those weaknesses—an easy win for home network security, since many routers have automatic notifications and updates built into the admin account’s interface these days. Even if you have a router that doesn’t make updates that simple, you can easily perform manual ones by going to your router’s support page, and looking to see what the latest firmware version is. If a newer one is available, download it and then follow the instructions for applying the update to your router.
Disable UPnP (and features that bypass firewall protection)
 TheIgel69 / Wikimedia Commons
TheIgel69 / Wikimedia Commons
A technical diagram of UPnP architecture. As a home user, you don’t need to dive this deep into the technical details for better network security. Just turn it off.
Universal Plug and Play (UPnP) is a common feature on routers that allows network devices to find each other easily. As an extension of this, UPnP can help when trying to get VOIP services and online gaming on consoles working properly—it allows devices from other networks to access them. Some routers also have what the manufacturer might call a “Demilitarized Zone,” or DMZ—a mode that allows all of a device’s ports to be exposed to the internet. It’s a more nuclear option than UPnP.
Any port exposed to the internet is a vulnerability. Windows has a built-in firewall for a reason: It protects your PC from malicious actors from trying to gain access, often in the hopes of using your machine to perform DDoS attacks. And if someone else is keeping your device busy, you won’t be able to use it.
Avoid leaving ports open on a device, and disable any DMZ-like feature. UPnP is often not necessary, either, so leave that off, too. Instead, use manual port forwarding.
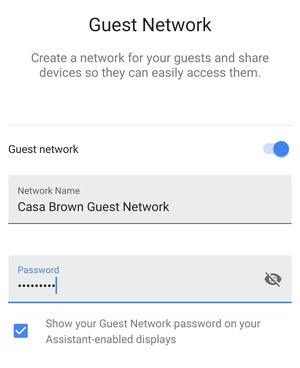
Set up a guest network for smart home devices
 PCWorld
PCWorld
An example of setting up a guest network from a simplified phone app interface.
A guest network is a feature on some routers where you can set up a separate SSID and password for access to your home network, and people on that network won’t be able to see devices (and their traffic) on your primary network.
By segmenting your guests’ internet access from your household’s, you can minimize snooping on the traffic of your home devices. A guest network is also a good hedge against insecure devices—like baby monitors, smart speakers, and other smart devices that can be put online but don’t often have strong security to prevent being taken over and then used in eavesdropping attacks.
Extra steps
Disable Wi-Fi access to your router’s admin account
Most people don’t log into their router’s administrator account often. And on some routers, you can restrict admin account access to devices on a wired ethernet connection only. So if you want to really lock down those privileges, turn that feature on. Afterward someone would need both physical access and a wired device to manage your router.
This setting is most ideal for people logging into the admin account via a PC. Devices like phones and tablets can still work, but you’ll need an appropriate dongle to connect an ethernet cable to the device.
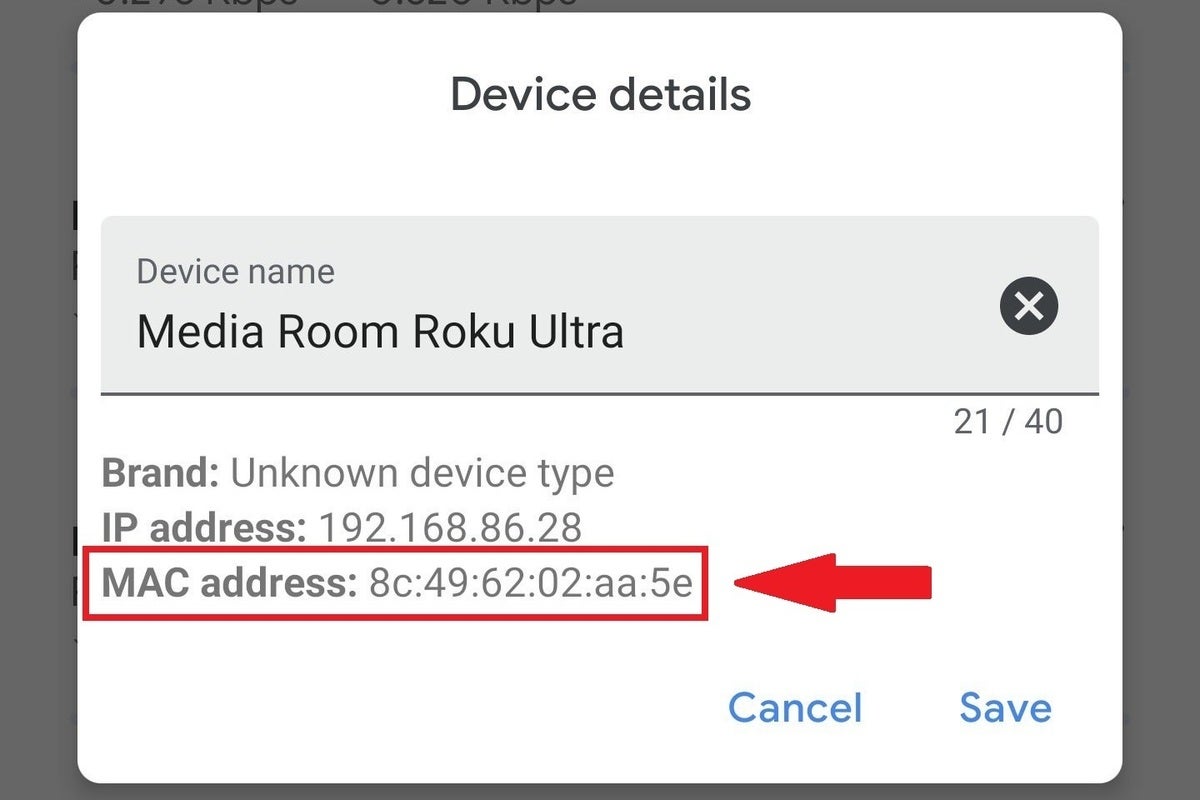
Enable MAC Filtering
 Michael Brown / IDG
Michael Brown / IDG
An example of a MAC address.
All internet-capable devices have a Media Access Control (MAC) address—a unique string of alphanumeric characters formatted as six pairs of characters connected by colons. A MAC address is how your PC, phone, or other gear identifies itself to your router.
You can make Wi-Fi available to specific devices based on MAC addresses. Known as MAC filtering, your router grants access if a MAC address is on its allow list. Like a bouncer checking a VIP list, your router will bar any device not on that list from connecting—even when it provides the correct Wi-Fi password.
Be aware that MAC filtering is more of a hindrance to someone who wants unauthorized access to your network as opposed to an extra iron-clad layer of protection. MAC addresses can be spoofed. So any device faking the MAC address of a device on the allow list can still connect to your router with your Wi-Fi password.
MAC filtering at home can also make you less anonymous while you’re out and about. The latest versions of Android and iOS use randomized MAC addresses to reduce your chances of being tracked by that identifier. Most people will choose to simply turn off that feature for MAC filtering, as the alternative is updating your router’s allow list with the new MAC address each time you want to connect to the Wi-Fi at home.


